Transportation System Cybersecurity
Vulnerability Analysis of Traffic Control System
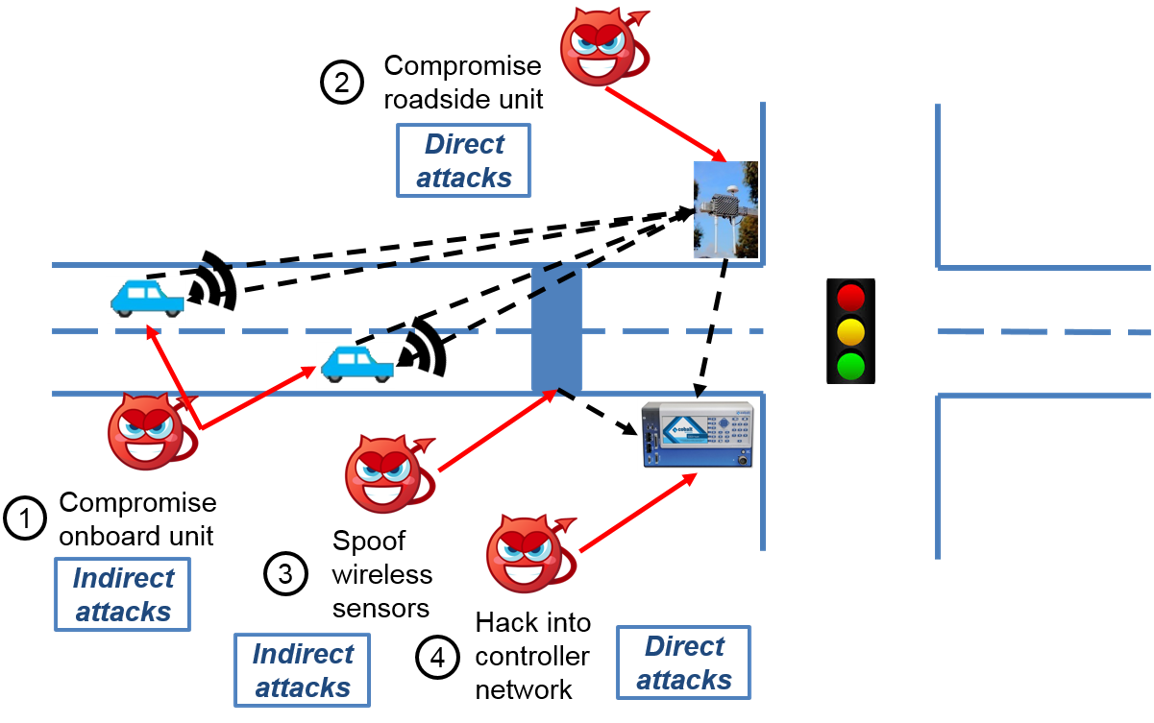
We investigate the vulnerability of traffic control system in a connected environment, where four typical elements including signal controllers, vehicle detectors, roadside units (RSUs), and onboard units (OBUs) are identified as the attack surfaces. We focused on attacking actuated and adaptive signal control systems by sending falsified data, which is considered as an indirect but realistic attack approach. The objective of an attacker is to maximize system delay with constraints such as budget and attack intensity.
Related Publications:
Huang, S., Feng Y., Wong, W., Chen, Q.A., Mao, Z.M., and Liu, H.X., Impact Evaluation of Falsified Data Attacks on Connected Vehicle Based Traffic Signal Control Systems. 2021. Third International Workshop on Automotive and Autonomous Vehicle Security (AutoSec) 2021 (Best Paper Award).
Chen, Q., Yin, Y., Feng, Y., Mao, Z.M., and Liu H.X.. Exposing Congestion Attack on Emerging Connected Vehicle based Traffic Signal Control. Network and Distributed System Security Symposium (NDSS), 2018.
Feng, Y., Huang, S., Chen, Q.A., Liu, H.X., and Mao, Z.M.. 2018. Vulnerability of Traffic Control System Under Cyber-Attacks Using Falsified Data. Transportation Research Record. Vol. 2672(1) 1-11.
Defense Solution based on Anomaly Detection
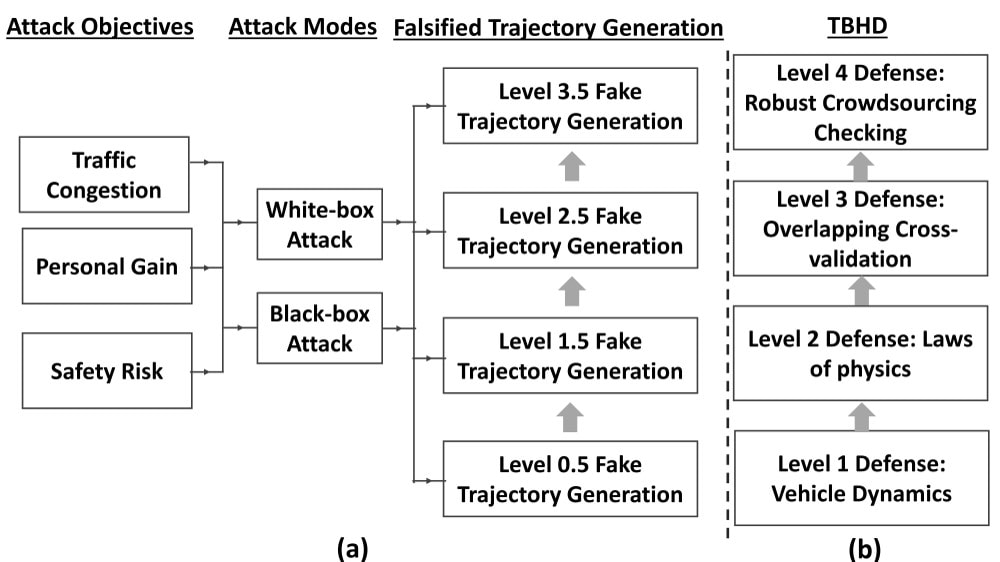
We look at the defense solutions by developing a trajectory-based hierarchical defense (TBHD) model to detect misbehaviors. The defense model consider. Te TBHD model consists of multiple hierarchies. Level 1 is a pointwise checking that checks if data elements in the received BSMs fall within their feasible ranges. Level 2 is a multiple-point checking that checks if the consecutive BSMs of one CV obey the laws of physics. Level 3 is a multiple-trajectory checking that checks if two CVs’ trajectories overlap with each other. Level 4 borrows methods from natural language processing (NLP) to cluster vehicle trajectories based on a robust crowd-sourcing scoring system.
Related Publications:
Huang, S., Feng, Y.,, Liu, H.X., 2021, A Data Driven Method for Falsified Vehicle Trajectories Identification by Anomaly Detection. Transportation Research Part C: Emerging Technologies. 128, p. 103196.
Wong, W., Huang, S., Feng, Y., Chen, A.Q., Mao, Z.M., and Liu, H.X, 2019. Trajectory-based Hierarchical Defense Model to Detect Cyber-attacks on Transportation Infrastructure. Transportation Research Board 98th Annual Meeting Compendium of Papers, Washington DC, 2019.
