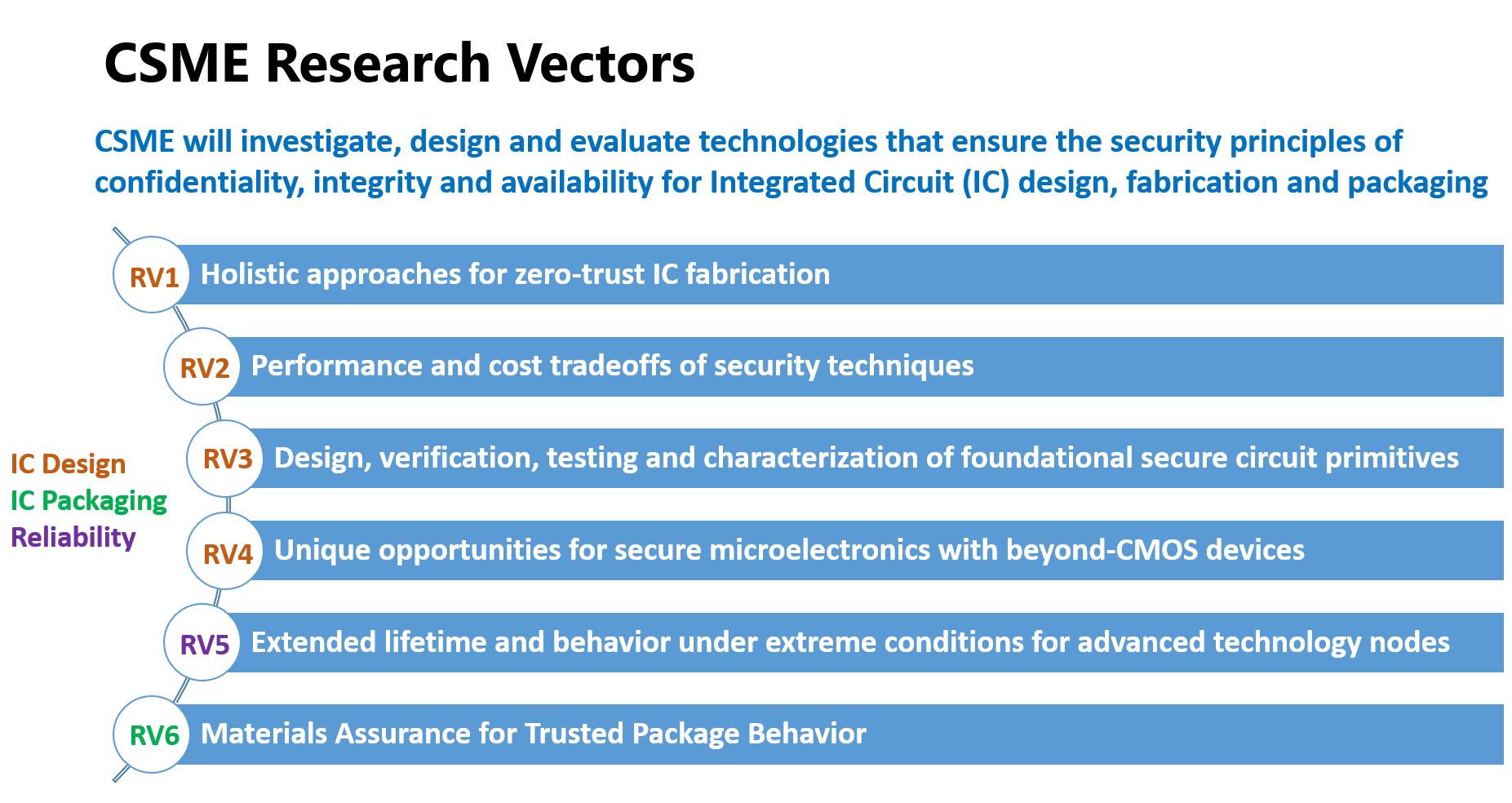
CSME aims to investigate, design and evaluate technologies that ensure the security of integrated circuits under a zero-trust model. To pursue this overarching goal, CSME’s research efforts will be organized into the six research vectors listed below.

VEDA: A Unified Pre/Post-Silicon Verification Platform for Quantifiable Assurance
PI: Swarup Bhunia; CoPI: Sandip Ray
In this project, we propose to develop a comprehensive infrastructure, VEDA (Verification based Design Assurance) to address this critical problem. The framework enables trust assessment and verification of a microelectronics device at different stages in its life cycle. VEDA is built to account for zero trust requirements from the ground up, including trust issues in IPs procured from an untrusted IP vendor as well as ICs fabricated by an untrusted foundry and provisioned or tested in an untrusted facility.

Security Quality Assurance against Side Channel Attack for Trusted Microelectronics and its Portability Across Technology
PI: Shreyas Sen
(A) On-chip Security Quality Monitor Design using BIST (Built-in-Self-Test), (B) Guarantee per device security quality using BIST + on-chip Tuning, (C) Provide security HVM quality estimate using small sample set (N=20-100) BIST data, and (D) Process Tampering, Cloning, Counterfeit identification using non-invasive EM SC signatures and BIST process monitors.

SARI: Security-Aware Reconfigurable Interposer
PI: Michel Kinsy
Under this project efforts, the PI is introducing a novel, reconfigurable on-interposer interconnect which enables user-defined security at runtime, bypassing fab-time attacks. The proposed methodology uses a new active reconfigurable interposer based 2.5-D design approach that enables integration time or user-side, hardware-assisted, security features programming. It decouples the security of the chiplet-based design from the individual chiplet fabrication or provenance, or even the interposer itself. It does this by imbuing the active interposer with reconfigurable fabric that can be programmed at integration and end-use stages to provide hardware root-of-trust security guarantees.

Zero-trust IPs through Interposer-based Integration
PI: Paul Gratz; Co-PIs: Jiang Hu, JV Rajendran
In this work we propose to leverage the advent of interposer-based, 2.5D integration to enable the concept of Zero-trust IP integration. In particular, we will explore novel techniques to show formal proof that IP blocks and the interposer have not been tampered with through a highly flexible and practical version of split-manufacturing we dub 2.5D Logic Redaction. Further we will look at mechanisms to leverage the interposer as a root-of-trust in 2.5D integrated systems, securing those chiplets for which trust cannot be otherwise established. We also will look at the assumed security of eFPGA-based redaction. We will develop an attack to retrieve the hardware IP with only black-box access to a programmed eFPGA, based on the effect of modern electronic design automation (EDA) tools on practical hardware circuits and leverage the observation to guide our attack.

Attack-resistant voltage and clocking infrastructure for SoCs
PI: Arijit Raychowdhury
Hardware cryptosystems are vulnerable to attacks from malicious agents through a variety of electrical and physical channels. To protect hardware from such attacks, power and clocking circuits need to be designed for resiliency against side-channel attacks. All these techniques come with very high area and power overhead, often eclipsing the hardware cost of the crypto-engine itself. While this can be an acceptable trade-off in microprocessors, the design space is quite different in mobile and IoT platforms that are severely limited in their power and area budgets. This calls for innovations in protection hardware for crypto-engines that are embedded in such devices. The problem is further exacerbated when we consider new crypto standards that are being developed to meet the demands of the embedded markets.

Protecting Physical and Logical Side-channels in Cryptographic Hardware and Accelerator-rich Computing Systems
PI: Kaushik Roy; Co-PI: Anand Raghunathan
Logical and physical side-channels are common causes of hardware vulnerabilities and security attacks in computing systems. Our project addresses side-channel attacks through three defense strategies: (i) We develop a machine learning based framework to detect the sources of power leakage in cryptographic hardware, enabling designers to pinpoint and eliminate such leakage, (ii) We propose a method of isolating state to address logical leakage channels that arise due to the use of shared accelerators in systems-on-chip (SoCs), and (iii) We propose an efficient method for machine learning with fully-homomorphic encryption by computing in the frequency domain.

RV2: Deep Learning based Cross-device and Cross-process Side Channel Analysis
Deep Learning based Cross-device and Cross-process Side Channel Analysis
PI: Sandip Ray; Co-PI: Swarup Bhunia
In this project, we will focus on optimizing the trace collection process and the impact of each individual trace. This will consist of two main goals, 1) an analysis of cross-device and cross-process side channel similarity; and 2) trace expansion and dataset maximization. We will accomplish these through three tasks: (A) Evaluation of Side Channel Behavior between Devices on the Same Process, (B) Cross-Process Side Channel Analysis, and (C) Trace Utility Maximization.

Low-Overhead Side-Channel Attack Resilient Open-Source Post-Quantum Cryographic Accelerators
PI: Shreyas Sen
The rapid advancement of quantum computing has compromised traditional public key cryptography (PKC), such as RSA. To address these quantum threats, NIST introduced Post-Quantum Cryptography (PQC) standards, including FIPS 203 and 204. Implementing PQC with robust side-channel attack (SCA) resilience is challenging, especially for resource-constrained IoT devices. This project focuses on developing low-overhead PQC cores with strong SCA countermeasures, emphasizing efficiency, low power consumption, and cryptographic flexibility.

Hierarchical Side-channel Leakage Assessment for Post Quantum Cryptographic Accelerators
PI: Patrick Schaumont
This project investigates a simulation-driven methodology for side-channel leakage assessment in Post-Quantum Cryptographic Accelerators. A hierarchical, top-down approach is well suited for the early identification of side-channel leakage sources, particularly during the exploration of countermeasures. The proposed assessment encompasses all modeling levels relevant to programmable SoC designs, extending down to the gate level. The methodology is applied to the Adam’s Bridge open-source implementations, with a focus on ML-DSA (Dilithium). The primary outcomes of the project will include a verified pre-silicon side-channel leakage assessment model for Adam’s Bridge and a proof-of-concept hardware demonstrator IC.

Polymorphic Logic – Obfuscation, Locking, and Reconfigurability
PI: Joerg Appenzeller; Co-PIs: Zhihong Chen; Mark Johnson
We propose the use of reconfigurable logic gates based on ambipolar transistors to obfuscate circuit designs. Different from obfuscation techniques that use many additional cells alongside the performing cells to hide the actual function of the circuit, polymorphic gates do not have the same overhead demand. This offers the opportunity for a more compact design and reduced power consumption. Moreover, polymorphic gates reveal their functionality only after the polarities of the power rails is properly chosen.

Measurement and Characterization of Semiconductor Process Variation Based Security IPs
PI: Shih-Lien (Linus) Lu
We propose to evaluate the power-up behavior of SRAM structures built using advanced CMOS nodes on integrated circuits such as CPU in deployed systems. Since caches are not directly accessible by software, we will investigate methods to interface with SRAM memory on other integrated units within the CPU that have direct software accessibility. After gathering measurements, we will focus on characterizing the data by examining systematic bias distributions and their impact on security IPs that leverage random variations to create security primitives.

Security Threats and Opportunities in Non-volatile Memory based Hardware Accelerator
PI: Shimeng Yu
We will investigate security vulnerabilities introduced by the non-volatility of weights being persistent in the hardware accelerators. There are two aspects of the threats: one is the data integrity in eNVMs and its robustness to environmental or manipulated changes (e.g. by adversary); the other is the data privacy as the valuable information (e.g. DNN model) is stored in the eNVMs even when the chip is powered off.

Using MRAM as Sensors for Side Channel Attacks
PI: Joerg Appenzeller; Co-PIs: Zhihong Chen; Mark Johnson
We propose the development of sensors to detect side-channel attacks aimed at MRAM devices by using the MRAM itself as a sensor. This work involves the following unique thrusts: (A) Explore quantitatively vulnerabilities of MRAM to DC and AC magnetic fields and temperature through a statistical analysis and modeling, (B) Define the desired MRAM access patterns to half-selected cells to identify SCAs and design a memory controller considering relevant timing constraints to interface with the external MRAM, and (C) Identify methods to create a data dump and/or transfer when SCAs are detected.

IC and Mission-Specific Aging Captured by the “Intrinsic Odometers”
PI: Muhammad A. Alam; Co-PI: Saeed Mohammadi
We will use a four-pronged measurement-based self-monitoring and accelerated test strategy for the specialized IC needed for government and non-standard-usage electronics. These include: (A) interconnect derived heating/thermometry, (B) stress-induced Iddq monitoring, (C) finger-printing of Supply-current transients and low-frequency noise thermometry, and (D) bond-pad watermarking.

Microstructure Fingerprinting for Secure Microelectronics
PI: Nikhilesh Chawla; Co-PI: Ganesh Subbarayan
In this project we address the issue of trusted packages by introducing the concept of a “microstructural signature” that can be easily detected and quantified using non-destructive x-ray and optical microscopy followed by n-point correlation function analysis. The concept relies on a particle filled adhesive layer that can be applied during manufacturing, signature particles inserted into die adhesive, thermal interface materials or other layers inherent in advanced packages. The distribution of particles (conductive or non-conductive) can be quantified to obtain a unique signature of the device involved.