Publications
Resilient Cyberinfrastructure
Malik, Raghav, Vidush Singhal, Benjamin Gottfried, and Milind Kulkarni. "Vectorized secure evaluation of decision forests." In Proceedings of the 42nd ACM SIGPLAN International Conference on Programming Language Design and Implementation (PLDI), pp. 1049-1063. 2021.
Resilient Cyber-Physical Systems
Wang, Sihan, Guan-Hua Tu, Xinyu Lei, Tian Xie, Chi-Yu Li, Po-Yi Chou, Fucheng Hsieh, Yiwen Hu, Li Xiao, and Chunyi Peng. "Insecurity of operational cellular IoT service: new vulnerabilities, attacks, and countermeasures." In Proceedings of the 27th Annual International Conference on Mobile Computing and Networking (Mobicom), pp. 437-450. 2021.
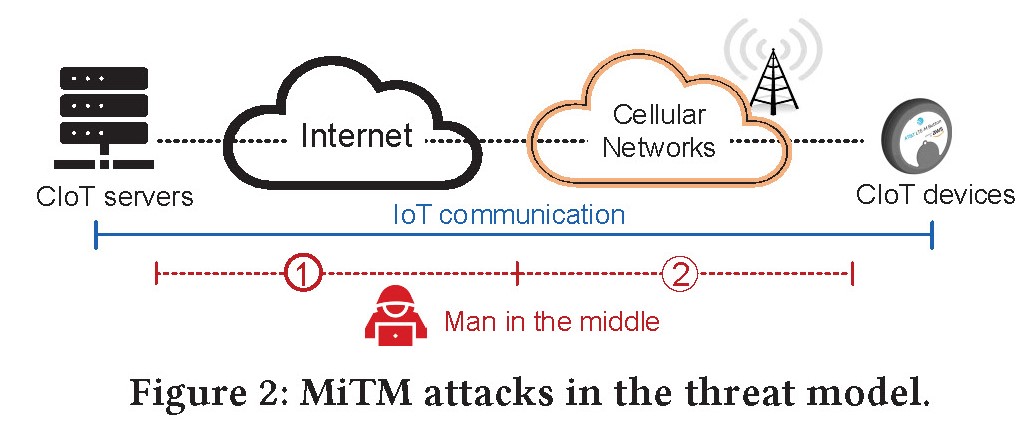
Insecurity of Operational Cellular IoT Service: New Vulnerabilities, Attacks, and Countermeasures
More than 150 cellular networks worldwide have rolled out massive IoT services such as smart metering and environmental monitoring. Such cellular IoT services share the existing cellular network architecture with non-IoT (e.g., smartphone) ones. When they are newly integrated into the cellular network, new security vulnerabilities may happen from imprudent integration. In this work, we explore the security vulnerabilities of the cellular IoT from both system-integrated and service-integrated aspects. We discover five vulnerabilities spanning cellular standard design defects, network operation slips, and IoT device implementation flaws. Threateningly, they allow an adversary to remotely identify IP addresses and phone numbers assigned to cellular IoT devices and launch data/text spamming attacks against them. We experimentally validate these vulnerabilities and attacks with three major U.S. IoT carriers. The attack evaluation result shows that the adversary can raise an IoT data bill by up to $226 with less than 120 MB spam traffic and increase an IoT text bill at a rate of $5 per second; moreover, cellular IoT devices may suffer from denial of IoT services.We finally propose, prototype, and evaluate recommended solutions.
Resilient Socio-Technical Systems
Jiao, Roger, Sesh Commuri, Jitesh Panchal, Jelena Milisavljevic-Syed, Janet K. Allen, Farrokh Mistree, and Dirk Schaefer. "Design Engineering in the Age of Industry 4.0." Journal of Mechanical Design 143, no. 7 (2021): 070801.
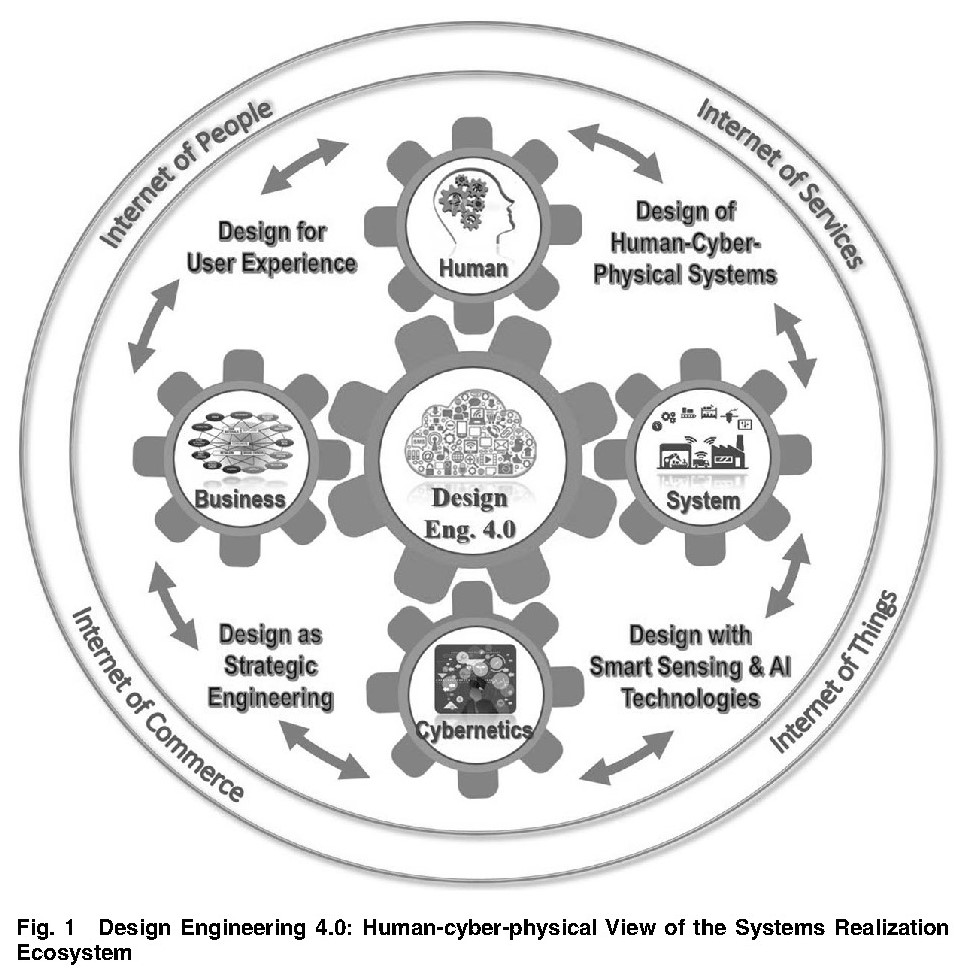
Design Engineering in the Age of Industry 4.0
Industry 4.0 is based on the digitization of manufacturing industries and has raised the prospect for substantial improvements in productivity, quality, and customer satisfaction. This digital transformation not only affects the way products are manufactured but also creates new opportunities for the design of products, processes, services, and systems. Unlike traditional design practices based on system-centric concepts, design for these new opportunities requires a holistic view of the human (stakeholder), artefact (product), and process (realization) dimensions of the design problem. In this paper we envision a “human-cyber-physical view of the systems realization ecosystem,” termed “ Design Engineering 4.0 (DE4.0),” to reconceptualize how cyber and physical technologies can be seamlessly integrated to identify and fulfil customer needs and garner the benefits of Industry 4.0.