Project Description
 |
Wireless camera networks are more complex than wireless sensor networks simply because cameras generate a lot more information than simple scalar sensors and also because cameras are directional devices. This research program, supported by Olympus, aims to uncover and solve the fundamental problems in wireless camera networks. |
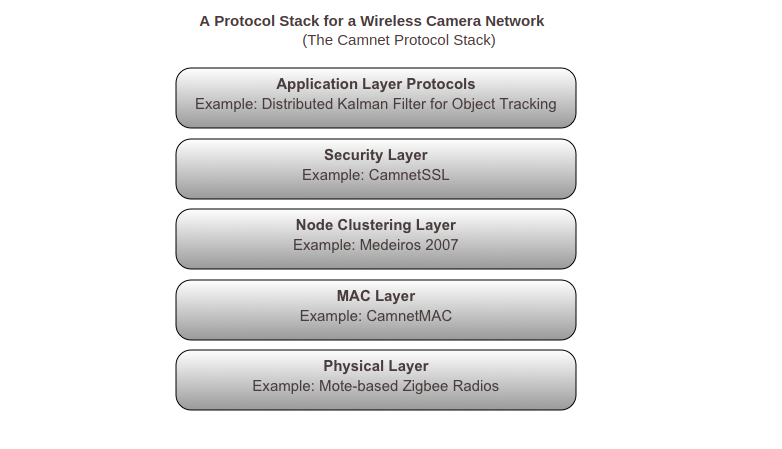
Our research envisions a protocol stack for the operation of wireless camera networks. In spirit, this is very much like the protocol stack for the TCP/IP networks --- but the similarity ends there. The engineering of the protocol stack for a wireless camera network is driven by a clustering protocol that allows the network nodes to cluster together so that information can be extracted from the image data in a cooperative manner. With the clustering protocol in place, one can envision higher application- level protocols for solving useful problems of interest, and lower-level protocols that operate at the MAC layer and that allow the clustering protocol to operate more efficiently.
Shown below is the protocol stack we are developing in our laboratory. We refer to this as the Camnet protocol stack. The heart of the stack is the node clustering protocol described in our publication Medeiros et al. [Medeiros 2007]. Since wireless networks are by nature wide open to intrusion, it is difficult to think of any meaningful application where security would not be an issue. We therefore envision a security layer on top of the clustering layer, as shown in the figure below. For this purpose, we are in the process of implementing a security protocol we call CamnetSSL. It is based on the ECC (Elliptic-Curve Cryptography) Diffie-Hellman for the generation of symmetric keys for fast and secure data transfer between the nodes. Below the clustering layer comes the MAC (Media Access Control) layer for the efficient operation of the clustering layer.
The MAC layer protocol, called CamnetMAC, uses a combination of TDMA and CSMA. TDMA is used to assign specific time slots to each node in a cluster and CSMA to allow new nodes to join a cluster and for inter-cluster communications when the border nodes of two neighboring clusters are within one-hop communication range. The time interval that is divided up by TDMA contains windows for CSMA communications to take place.
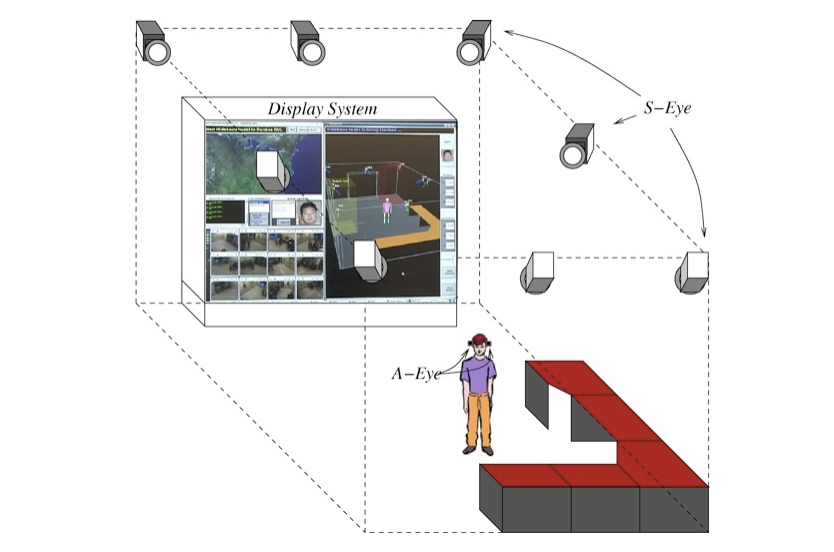
Our application layer protocols entails the integration of three different agent-based sensing modules: S-Eye, A-Eye, and T-eye. A group of S-Eyes will be rigidly fixed to an environment to gather and integrate spatial information and generate an abstract level of knowledge of dynamic environments and objects. An A-Eye will be attached to a user to observe an outer-world (environment) with a viewpoint of the user's interest. Finally, T-Eye will observe the internal physiological and/or mental states of the human user. The integration of these three modules will provide a required level of privacy and security to the users in the environment. Although we intend to develop all three types of these sensing modules in the A-Cubed Project, our immediate goal will be to focus on only S-Eye and A-Eye. See Figure 1 for a sketch describing the basic concept and initial goals of the A-Cubed project.

Figure 1: A sketch describing the basic concept and initial goals of A-Cubed project
We have several other projects that are under the A-Cubed project. The links to these projects are also available below.
Project Team
| Kihyun Hong | Donghun Kim |
| Akio Kosaka | Henry Medeiros |
| Johnny Park | Paul Shin |
| Gaurav Srivastava | Josiah Yoder |
Publications
-
Online Distributed Calibration of a Large Network of Wireless Cameras Using Dynamic Clustering
Henry Medeiros, Hidekazu Iwaki, and Johnny Park, "Online Distributed Calibration of a Large Network of Wireless Cameras Using Dynamic Clustering," Second ACM/IEEE International Conference on Distributed Smart Cameras, September 7-11, 2008. -
A Novel Evidence Accumulation Framework for Robust Multi Camera Person Detection
Hidekazu Iwaki, Gaurav Srivastava, Akio Kosaka, Johnny Park, and Avinash Kak, "A Novel Evidence Accumulation Framework for Robust Multi Camera Person Detection," ACM/IEEE International Conference on Distributed Smart Cameras, 2008. -
Efficient Implementations of Contour Extraction and Curvature Scale Space Representation on SIMD-based Smart Cameras
Paul J. Shin, Xinting Gao, Richard Kleihorst, Johnny Park, and Avinash C. Kak, "Efficient Implementations of Contour Extraction and Curvature Scale Space Representation on SIMD-based Smart Cameras," ACM/IEEE International Conference on Distributed Smart Cameras, 2008. -
Distributed Object Tracking Using a Cluster-Based Kalman Filter in Wireless Camera Networks
H. Medeiros, J. Park, and A. C. Kak, "Distributed Object Tracking Using a Cluster-Based Kalman Filter in Wireless Camera Networks," in IEEE Journal of Selected Topics in Signal Processing, vol. 2, no. 4, pp. 448-463, August 2008. -
A Parallel Color-Based Particle Filter for Object Tracking
H. Medeiros, J. Park, and A. C. Kak, "A Parallel Color-Based Particle Filter for Object Tracking," in the Fourth IEEE Workshop on Embedded Computer Vision (in conjunction with CVPR), June 23-28, 2008. -
A QoS Evaluation Testbed for MAC Protocols for Wireless Camera Networks
P. J. Shin, J. Park, and A. C. Kak, "A QoS Evaluation Testbed for MAC Protocols for Wireless Camera Networks," ACM/IEEE International Conference on Distributed Smart Cameras, 2007 -
A Light-weight Event-driven Protocol for Sensor Clustering in Wireless Camera Networks
H. Medeiros, J. Park, and A. C. Kak, "A Light-weight Event-driven Protocol for Sensor Clustering in Wireless Camera Networks," First ACM/IEEE International Conference on Distributed Smart Cameras, September 25-28, 2007. -
A Look-up Table Based Approach for Solving the Camera Selection Problem in Large Camera Networks
J. Park, P. C. Bhat, and A. C. Kak, "A Look-up Table Based Approach for Solving the Camera Selection Problem in Large Camera Networks," Workshop on Distributed Smart Cameras, in conjunction with ACM SenSys'06, 2006 -
Hierarchical Data Structure for Real-Time Background Subtraction
J. Park, A. Tabb, and A. C. Kak, "Hierarchical Data Structure for Real-Time Background Subtraction," in Proceedings of IEEE International Conference on Image Processing, 2006. -
Human Motion Tracking With Multiple Cameras Using a Probabilistic Framework for Posture Estimation
Ruth Devlaeminck, "Human Motion Tracking With Multiple Cameras Using a Probabilistic Framework for Posture Estimation," Master's Thesis, School of Electrical and Computer Engineering, Purdue University, August 2006.