 Multimedia Security Research at Purdue University
Multimedia Security Research at Purdue University
 Multimedia Security Research at Purdue University
Multimedia Security Research at Purdue University
Many approaches are available for protecting digital data; these include encryption, authentication and time stamping. One approach to protect images is to add an invisible structure to the image data itself that can be used to authenticate it. These structures are known as digital watermarks. If the image is copied and distributed, the watermark is distributed along with the image. This is in contrast to the (easily removed) ownership-information fields allowed by the MPEG-2 syntax. Figure 1. shows the general watermarking embedding procedure.
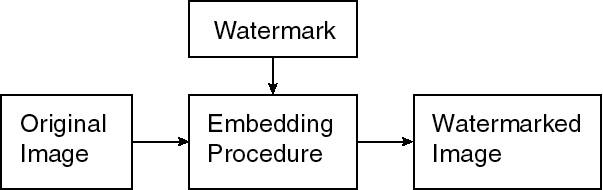
Figure 1. Top-level image watermarking procedure.
Several papers are available which provide readable, top-level overviews of digital watemrarking:
![]() R. B. Wolfgang, C. I. Podilchuk, and
E. J. Delp, "Perceptual Watermarks for Digital Images and Video", submitted
to the Proceedings of the IEEE, 1998. The readme
file , PDF
file, and the ftp
site.
R. B. Wolfgang, C. I. Podilchuk, and
E. J. Delp, "Perceptual Watermarks for Digital Images and Video", submitted
to the Proceedings of the IEEE, 1998. The readme
file , PDF
file, and the ftp
site.
![]() R. B. Wolfgang and E. J. Delp, "Overview
of Image Security Techniques with Applications in Multimedia Systems,"
Proceedings of the SPIE Conference on Multimedia Networks: Security, Displays,
Terminals, and Gatweys, Vol. 3228, November 2-5, 1997, Dallas, Texas, pp.
297-308. The readme
file, compressed
postscript file, PDF
file, and the ftp
site.
R. B. Wolfgang and E. J. Delp, "Overview
of Image Security Techniques with Applications in Multimedia Systems,"
Proceedings of the SPIE Conference on Multimedia Networks: Security, Displays,
Terminals, and Gatweys, Vol. 3228, November 2-5, 1997, Dallas, Texas, pp.
297-308. The readme
file, compressed
postscript file, PDF
file, and the ftp
site.
 Variable-Watermark
Two-Dimensional Algorithm (VW2D)
Variable-Watermark
Two-Dimensional Algorithm (VW2D)As part of the marking procedure, the inner (dot) product between each watermark block and corresponding marked image block is computed. Testing consists of computing the inner product between a test image block and the mark, and subtracting this from the previously stored value. This block-based procedure allows us to localize changes made to an image down to an 8 x 8 pixel resolution. A user-defined threshold on the magnitude of the change determines whether a block is unacceptably altered from the original. This allows minor changes to a particular block to be overlooked in examining the authenticity of the entire image. Figure 2 shows the testing procedure for VW2D.
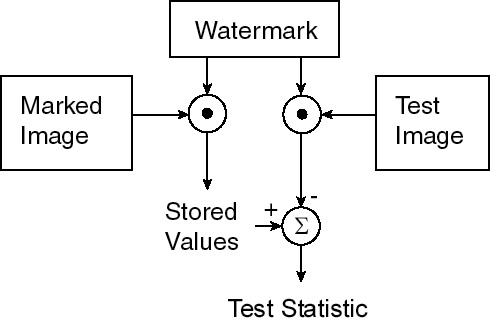
Figure 2. VW2D testing procedure.
The VW2D algorithm has been shown to detect linear and non-linear filtering, and JPEG compression. Sample images, and the corresponding watermark and user-key file are available.
![]() R. B. Wolfgang and E. J. Delp, "A Watermark
for Digital Images," Proceedings of the IEEE International Conference on
Image Processing, September 16-19, 1996, Lausanne, Switzerland, pp. 219-222.
The readme
file, compressed
postscript file, PDF
file, and the ftp
site.
R. B. Wolfgang and E. J. Delp, "A Watermark
for Digital Images," Proceedings of the IEEE International Conference on
Image Processing, September 16-19, 1996, Lausanne, Switzerland, pp. 219-222.
The readme
file, compressed
postscript file, PDF
file, and the ftp
site.
![]() R. B. Wolfgang and E. J. Delp, "A Watermarking
Technique for Digital Imagery: Further Studies," Proceedings of the International
Conference on Imaging Science, Systems, and Technology, June 30 - July
3, 1997, Las Vegas, pp. 279-287. The readme
file, compressed
postscript file, PDF
file, and the ftp
site.
R. B. Wolfgang and E. J. Delp, "A Watermarking
Technique for Digital Imagery: Further Studies," Proceedings of the International
Conference on Imaging Science, Systems, and Technology, June 30 - July
3, 1997, Las Vegas, pp. 279-287. The readme
file, compressed
postscript file, PDF
file, and the ftp
site.
The image-adaptive watermarks are based on the robustness of the basic spread-spectrum technique. The spread-spectrum technique embeds a normally distributed zero mean pseudorandom sequence, W, into the transform coefficients (DCT or wavelet) of an original luminance image X. To verify a (possibly altered) marked image Z, one first obtains the normalized correlation coefficient (the test statistic) between the watermark W and the version of the watermark extracted from Z. A value near 1 indicates the presence of the mark; a small value (< 0.1) indicates that the watermark under test is not in the image Z, or that the image has been severely (and visibly) degraded to the point of removing the watermark.
The work in image-adaptive watermarking shows that using visual models in the embedding scheme can produce an even more robust watermark than the standard spread-spectrum technique. Specifically, visual models allow the user to raise or lower the amplitude of the watermark according to the image content (hence the name, image-adaptive). These visual models provide thresholds for how much a given transform coefficient can change, before such changes are noticeable under standard viewing conditions. Figure 3 shows the procedure for image-adaptive watermarking.
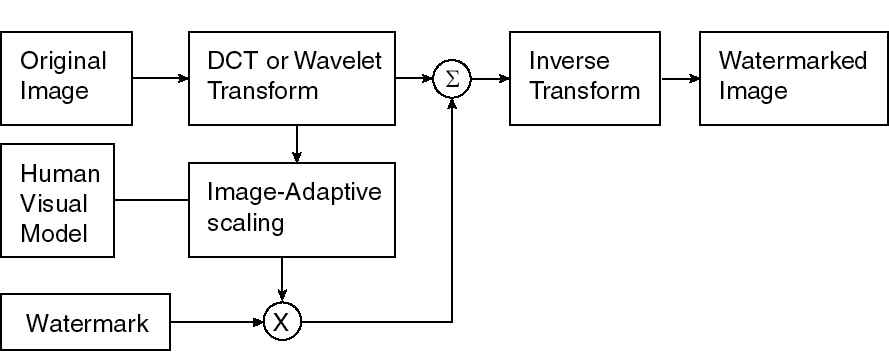
Figure 3. Image-adaptive watermarking procedure.
Several papers on spread-spectrum and image-adaptive watermarking are listed below. Sample images, and their corresponding watermarks are also available.
![]() I. J. Cox, J. Kilian, F.T. Leighton
and T. Shamoon, “Secure spread spectrum watermarking for multimedia,” IEEE
Transactions on Image Processing, vol. 6, no. 12, pp. 1673-1687, December,
1997.
I. J. Cox, J. Kilian, F.T. Leighton
and T. Shamoon, “Secure spread spectrum watermarking for multimedia,” IEEE
Transactions on Image Processing, vol. 6, no. 12, pp. 1673-1687, December,
1997.
![]() C. Podilchuk and W. Zeng, “Image-adaptive
watermarking using visual models,” IEEE Journal on Selected Areas in Communications.
vol. 10, no. 4, pp. 525-540.
C. Podilchuk and W. Zeng, “Image-adaptive
watermarking using visual models,” IEEE Journal on Selected Areas in Communications.
vol. 10, no. 4, pp. 525-540.
![]() R. B. Wolfgang, C. I. Podilchuk, and
E. J. Delp, "Perceptual Watermarks for Digital Images and Video", submitted
to the Proceedings of the IEEE, 1998. The readme
file , PDF
file, and the ftp
site.
R. B. Wolfgang, C. I. Podilchuk, and
E. J. Delp, "Perceptual Watermarks for Digital Images and Video", submitted
to the Proceedings of the IEEE, 1998. The readme
file , PDF
file, and the ftp
site.
![]() R. B. Wolfgang, C. I. Podilchuk, and
E. J. Delp, "The Effect of Matching Watermark and Compression Transforms
in Compressed Color Images," Proceedings of the IEEE International Conference
on Image Processing, October 4-7,1998, Chicago, Illinois. The
readme
file, compressed
postscript file, PDF
file, and the ftp
site.
R. B. Wolfgang, C. I. Podilchuk, and
E. J. Delp, "The Effect of Matching Watermark and Compression Transforms
in Compressed Color Images," Proceedings of the IEEE International Conference
on Image Processing, October 4-7,1998, Chicago, Illinois. The
readme
file, compressed
postscript file, PDF
file, and the ftp
site.
We would like to knowledge support from Digimarc for supporting our work in video watermarking. We also acknowlegde the Center for Education and Research in Information Assurance and Security (CERIAS) at Purdue University.
A complete set of recent publications at VIPER.